Renewing an Existing SSL/TLS Certificate In IIS

Renewing a certificate sounds like it should be easier than creating a brand new one. But for some reason, (for me, at least) it seemed to take even more steps. My hope is this tutorial will help someone else navigating the fun and exciting world of encryption and certificates.
Background
I was recently tasked with renewing a GoDaddy certificate on a Windows IIS server whose certificate was soon to expire. I was essentially given (1) admin access on a windows server and (2) a certificate bundle. I did not have an existing CSR and I was (at first) not sure where to find a private key.
Now normally, when you install a certificate for the very first time, you generate a private key along with a CSR (Certificate Signing Request). The CSR is sent along to a Certificate Authority (like GoDaddy, DigiCert, or Let’s Encrypt) who signs the request and sends you back one or more signed certificates. At this point, you generally opt to “complete” the signing request for your existing CSR (on your server) and then the cert is ready to use.
The problem with renewing an existing certificate is there’s no associated CSR. So when you’re given the updated certificates, they need to be manually paired with your existing private key before applying them. Which also may require extracting your private key first.
Overview
- Step 1) Extracting an Existing Private Key
- Step 2) Creating a New PFX File
- Step 3) Applying the New Cert
Step 1) Extracting an Existing Private Key
Unless you manage your private keys somewhere specific and you already have access to the one in question, you may need to start by extracting your existing private key.
To do this, log in to your IIS server and open up “Internet Information Services (IIS) Manager“

Click on the name of your server in the left panel
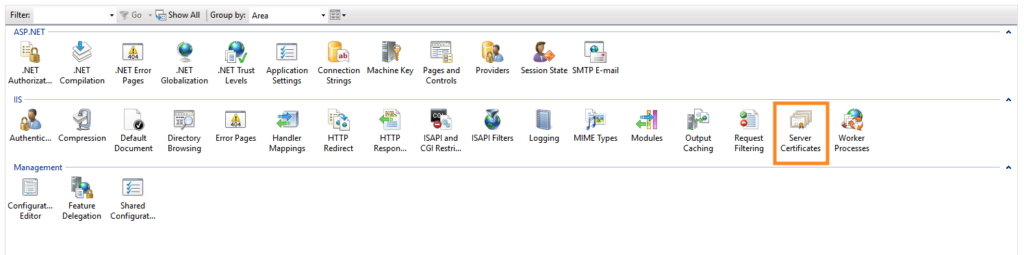
Click on “Server Certificates” Under “IIS”
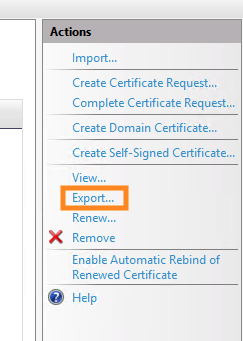
Click “Export” in the Actions panel
Click the three dots to the right of the “Export to:” box
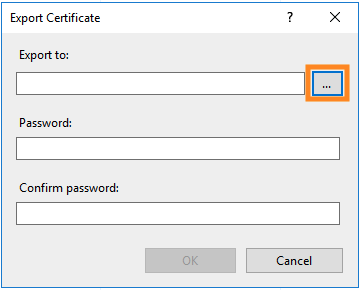
Choose a name for your exported file and a location, then click Open
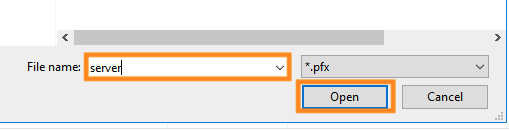
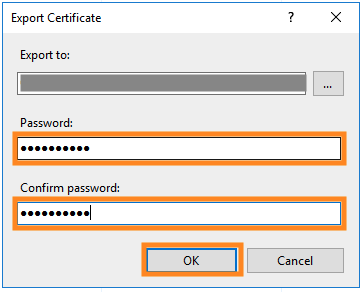
Now, choose a password to protect your exported file and click OK.
Note: This can be anything that you’ll remember in the next 10 minutes. You’ll just need it in the upcoming steps to access this file. It’s best to make it something safe.
Now you’ll need a way of extracting the private key from this file. In this tutorial, I will be using the popular utility “OpenSSL” on a Mac.
To install OpenSSL
On a Mac
If you have the homebrew package manager installed, you can install it using this terminal command:
brew install opensslOn Windows
You can find an installer through the OpenSSL wiki page.
Obtaining the private key
Once OpenSSL is installed, run the following command:
openssl pkcs12 -in <server.pfx> -nocerts -out <server.key><server.pfx> is the PFX file that you just extracted
<server.key> is a name for your extracted private key
This command should prompt you for the password that you just set for your extracted PFX file. Then, it will prompt you twice for a new password to set for the resulting private key. You can use the same password for this if you’d like, or choose a new one.
You should now have your private key.
Step 2) Creating a New PFX File
Now you have all the ingredients you need for your new cert: your private key and the updated cert(s) from your CA. But IIS expects all of these files to be neatly packaged up inside a single PFX file. In this step, we’ll use another openssl command to create the PFX file.
Run the following command to create a PFX file:
openssl pkcs12 -export -out <certificate.pfx> -inkey <server.key> -in <certificate.crt> -certfile <more.crt><certificate.pfx>is the name of the pfx file that you are creating<server.key>is the private certificate that you extracted<certificate.crt>is the signed certificate that you got from your CA<more.crt>is any additional cert or bundle from your CA
Note: the -certfile <more.crt> part is optional. This is where you would put any bundle or intermediary certificate given to you from your CA.
This command should prompt you once for the password that was set for your private key. Then it will prompt you twice to set a new password for the resulting PFX file. Again, here you can use the same password again or make a new one if you’d like.
You should now have a new PFX file!
Step 3) Applying the New Cert
Now all that’s left is importing your new PFX file to IIS and applying it to your site.
First, move the new PFX file over to your IIS server (if it’s not already there).
Now, go back in to IIS manager, select your server’s name in the left panel, and click on “Server Certificates” under “IIS”. Here, click “Import…” in the Actions panel.
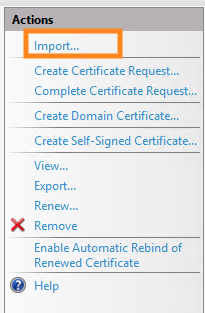
Click the three dots to the right of the “Certificate file” box
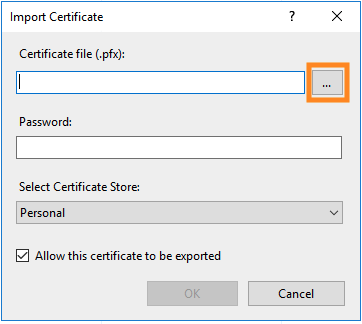
Choose your new PFX file and click “Open“
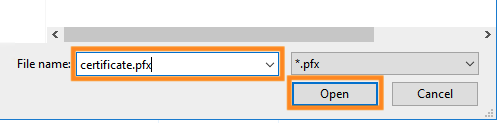
Enter the password that you set for your PFX file and select an appropriate Certificate Store (for me, it was Web Hosting, but may be different for you). Then select “OK“.
Your new certificate should show up in the list.
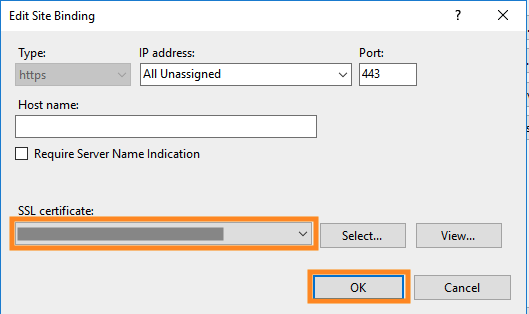
Now all you have to do is re-bind your site to the new certificate. To do this, open up the folders on the left panel and select the name of your site
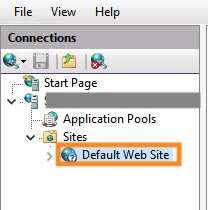
Within the “Actions” panel, select “Bindings…“
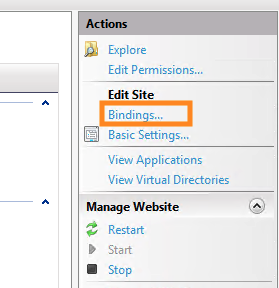
Double-click on “https“
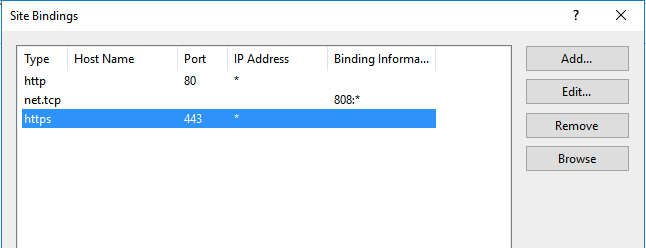
Now select your new certificate from the drop-down and click “OK” to apply the new certificate!